Base de Datos en la Nube

Hostman: Compromiso con la simplicidad y precios accesibles
cargos mensuales
cargos mensuales
base diaria/semanal
mensual/por hora
10 TB/mes
Soluciones de bases de datos personalizadas para cada necesidad
MySQL
PostgreSQL
Redis
OpenSearch
ClickHouse
Kafka
RabbitMQ
Documentation
¿Qué es una base de datos en la nube?
Comienza con la plataforma de bases de datos en la nube de Hostman
Precios transparentes para tus necesidades y costos predecibles

Cada plan incluye ancho de banda gratuito
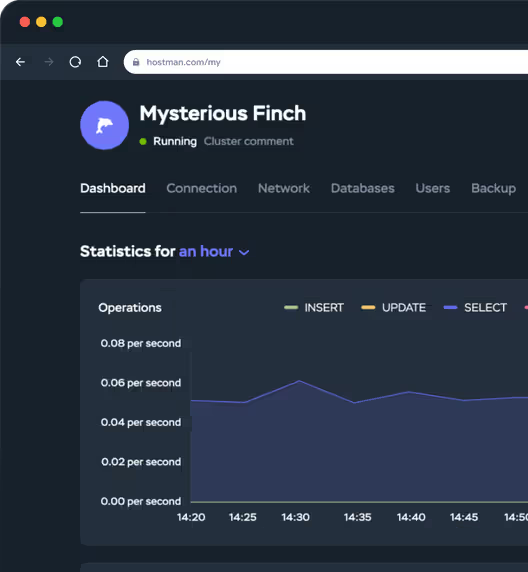
Un panel para gobernarlos a todos
Lo que dicen
nuestros usuarios
"Reseña Integral de Hostman sobre Simplicidad y Potencial"
"¡Una combinación perfecta para todos los servicios en la nube!"
"Experiencia de Usuario Sobresaliente"
"¡Excelencia en la Nube Simplificada!"
"Solución de Hosting Fácil y Sencilla para Aplicaciones Web"
"Utilizar Diferentes Servicios de Motor de Bases de Datos Ofrecidos por Hostman es Conveniente para los Casos de Uso de mi Organización"
"Hostman es ideal para mí"
"Página perfecta"
"Simplificando el Despliegue en la Nube con Fortalezas y Áreas para Mejorar"
"Despliegue Simplificado con Espacio para Mejoras"
¿Listo para comenzar?
la gestión de bases de datos en la nube con Hostman.
Empieza a convertir tus ideas en soluciones con los productos y servicios de Hostman
Servidores en la Nube
Aplicaciones
Kubernetes
Firewall
Más de 500 empresas y desarrolladores confían en Hostman
Red global de centros de datos de Hostman

Explora más sobre las bases de datos en la nube de Hostman
Cómo usar GitHub Copilot con Python
Cómo instalar y usar el gestor de paquetes Yarn para Node.js
Ejemplos de la directiva location en Nginx
Cómo Instalar y Usar ripgrep: guía paso a paso para búsquedas eficientes
Cómo restablecer la contraseña root de MySQL: guía paso a paso
Respuestas a tus preguntas
Ofrecen seguridad de primer nivel con cifrado, controles de acceso y auditorías regulares para proteger sus datos.
Soporta bases de datos relacionales (MySQL, PostgreSQL) y NoSQL (MongoDB, Redis), con flexibilidad total para cualquier proyecto.
Sí, Hostman permite escalar recursos al instante para manejar picos de tráfico sin esfuerzo.
Contamos con backups automáticos, snapshots programados y recuperación punto en el tiempo para restauración fiable.
Pago por uso: solo pagas por el almacenamiento y la potencia que utilizas realmente.
No, nuestro failover automático y actualizaciones continuas mantienen la base de datos disponible 24/7.
Sí, con nuestro soporte y herramientas de migración, la transferencia es rápida y con mínima interrupción.
Brindamos soporte técnico 24/7 para rendimiento, configuración, resolución de problemas y optimización.
Sí, puedes conectar fácilmente herramientas de terceros para mejorar la funcionalidad de tu base de datos.
Utilizamos cifrado de extremo a extremo y controles de privacidad estrictos para cumplir con las normas de protección.
Incluye monitoreo en tiempo real, ajuste de rendimiento y alertas automáticas para mantener la base de datos óptima.
Lleva tu base de datos
al siguiente nivel
para ayudarte a encontrar la solución perfecta para tu negocio y
apoyarte en cada paso del camino



